VPN

Effieciency, Productivity and Growth - Quickbooks Vs NetSuite
Why stay with software that holds your business back when you could use a system that empowers your business? Improve...

Transforming Security in the Mobile Cloud Era
In the age of digital transformation, maintaining secure interactions among users, applications, and...

End-point Log management
Deploying a robust log management solution on end-points can be challenging. Monitoring remote end-points...

The SMB Opportunity for MSPs: 2021-2026
According to new research from ConnectWise, MSP industry trends show that SMBs will create over $90 billion...

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

The State of Electronic Signature
Today's organisations can't wait any longer to make the digital transformation. It's no longer simply...

Trusted Access Report
As global conflicts spill into the digital realm, protecting people through to the enterprise is increasingly...

The VMware Guide to Disaster Recovery Readiness
When it comes to data, planning for the unexpected is of paramount importance—especially today. But...

Windows Server 2019 and PowerShell All-in-One For Dummies
Windows Server 2019 and PowerShell All-in-One For Dummies offers a single reference to help you build...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

The Pitfalls of SASE Vendor Selection: Features vs. Strategic Outcomes
After speaking with 1000s of IT pros, we've learned that success with SASE is only achieved when it meets...
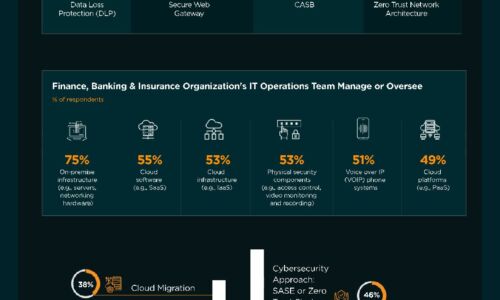
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

IDC Whitepaper: Achieving Network Modernization for the Decade Ahead
Every organization is now defined by the digital services it delivers. From engaging customers with new...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
