VPN

Enduring from Home: COVID-19’s Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

A Tiered Framework For Cyber Threat Levels
If you're a 'Trekkie' you know that 'shields' refer to advanced technology to protect starships, space...

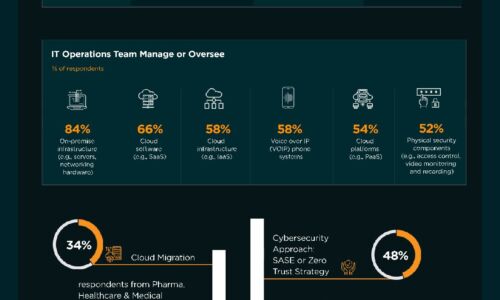
Your guide to small office IT success
Providing a great IT experience for your office doesn't have to be a challenge. Illustrating different...

Protecting The End User
A people-centric approach to managing vulnerability, attacks and privilege. Organisations are spending...

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

Three Top Trends in Higher Ed IT for 2021 and Beyond
We've had a tough 2020, but the ability to work and learn online from anywhere has been popular with...

7 Ways to Work from Anywhere
Bring security and speed to the office of the future Following a massive global influx of remote work,...

The Essential Guide to Storage for Virtualisation
There are plenty of proof points, and you're one of them—if your storage met your needs, you wouldn't...

The Total Economic Impact™ Of VMware Workspace ONE for Windows 10
The purpose of this study is to provide readers with a framework to evaluate the potential financial...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.