VPN
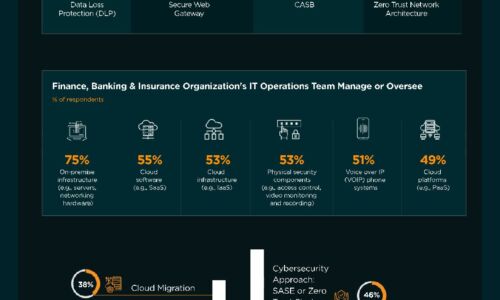
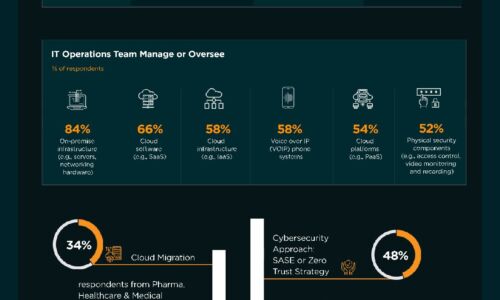
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Reinventing work How leading
We're coming off one of the most challenging years in business history. The pandemic forced every company...

What You Don't Know Can Hurt You: Expert advice on measuring risk
Managing risks begins with measuring risks. But how do you measure risks accurately? How do you share...

When Networks Meet The New Tomorrow
This paper looks at IT priorities that organizations will need to address now and in the new tomorrow: +...

Brian Madden's Playbook for Your Journey to the Cloud
Brian Madden, End-User Computing industry analyst and VMware resident expert, explains the big picture...

Protecting your content against cyber threats and data loss
How the Content Cloud safeguards your most valuable information Your business runs on content — but...

Industrial IoT for Predictive Maintenance
Discover the benefits and challenges of Industrial IoT (IIoT) enabled predictive maintenance, and how...

Privilege Access Management Buyers' Guide
Security breaches show no signs of slowing, and credential theft is the number one attack vector. Privileged...

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.