VPN

Centrify Zero Trust Privilege and Password Vaults
Privileged Identity Management (PIM) solutions are based on a variety of fundamental technologies, with...

Security's Privilege Crisis
Despite spending $114B on cybersecurity in 2018, the onslaught of security breaches continues unabated.1...

Five Lessons Learned from the Pivot to a Distributed Workforce
Today, it is increasingly important to enable your employees to work remotely. Working remotely gives...

2022 State of the Threat: A Year in Review
In 2022, ransomware remained the most prevalent form of attack. In investigations by Secureworks® incident...

A CIO's Guide to Accelerating Secure Digital Transformation
Cloud transformation is imperative, and it's the CIO who is under pressure to make sure the business...

Security Starts Here: Privileged Access Management
The threat of a security incident or critical error is very real, and it's something that auditors are...
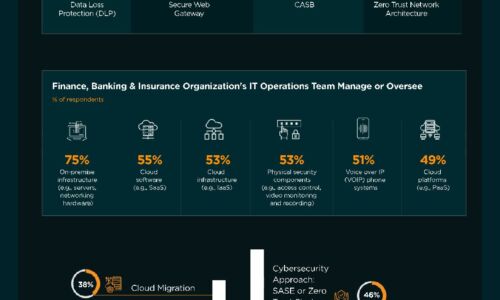
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Brute Force: Guide to Mitigating Attacks
A brute force attack is when an attacker attempts to gain access to an environment by identifying valid...

Dell EMC PowerStore: Data-centric, Intelligent, Adaptable Storage
This report provides a brief introduction to Dell EMC's PowerStore mid-range storage appliance and documents...

Your guide to small office IT success
Providing a great IT experience for your office doesn't have to be a challenge. Illustrating different...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



