Security Management

20 Examples of Smart Cloud Security
Smart cloud security provides critical capabilities such as governing access and activities in sanctioned...

Key Principles and Strategies for Securing the Enterprise Cloud
Customers are turning to the cloud to reduce capital expenses and increase agility as part of their digital...

Delivering Real-time Cloud Security Without Trading Off Performance
There has been a long-standing tradeoff between security and performance, and security often gets the...

Protecting the ATM Network with Fortinet
Protecting a network of geographically dispersed automated teller machines (ATMs) is a key challenge...

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

Is Your WAF Keeping Pace with Today’s Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Incident Response Use Cases
According to an IBM study, the vast majority of organisations surveyed are unprepared to respond effectively...

Internal Firewalls for Dummies Guide
Organizations can no longer rely on edge firewalls alone to provide network security. Once attackers...
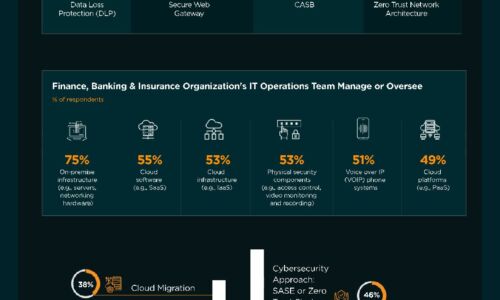
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

Accelerating Digital Transformation through Hyper-Converged Solutions
How can organizations simplify IT in order to improve business agility, enhance financial return on investment,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


