Security Management

LogRhythm for SWIFT Customer Security Controls Framework
Society for Worldwide Interbank Financial Telecommunication (SWIFT) facilitates a huge number of financial...

The Business Value of Red Hat Enterprise Linux
Linux has firmly established itself as a preferred delivery vehicle for modern applications, in addition...
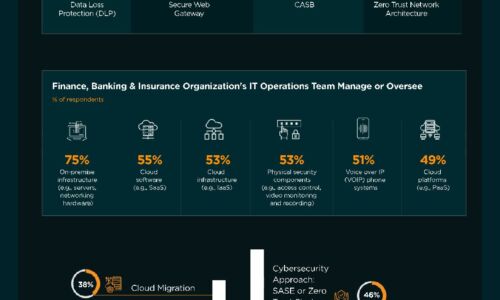
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Top 5 Ways to Simplify Data Protection with Microsoft Azure
Read this white paper to find out five ways that you can simplify data protection with Microsoft Azure,...

Ransomware Prevention and Remediation
The global damage costs of ransomware are projected to reach $20 billion in 2021. This includes not only...

Encryption, Privacy, and Data Protection: A Balancing Act
The Business, Privacy, and Security Mandates for Comprehensive SSL/TLS Inspection. Enterprise IT leaders...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...

Decoupling security from the network: The evolution of segmentation
You rely on the network to deliver applications. But as IT scales in size, connectivity, and environments...

BlackBerry Guard
Many businesses overlook or underinvest in managed detection and response (MDR), a critical aspect of...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

