Security Management

Aligning Cyber Skills To The MITRE ATT&CK Framework
The MITRE ATT&CK Framework is a comprehensive matrix of tactics and techniques used by threat hunters,...

Linux All-In-One For Dummies, 6th Edition
Inside, over 500 pages of Linux topics are organized into eight task-oriented mini books that help you...

Centralised Control Simplifies Management, Boosts Security
Aquila Heywood wanted to update its privileged access management processes to increase data security...

32 Security Experts on Changing Endpoint Security
For many companies, the modern business environment has become a mobile workplace in which employees...

The 4 Benefits of VPN Elimination
The corporate perimeter as you know it no longer exists. Virtual private network (VPN) vulnerabilities...

BlackBerry Guard: Solution Brief
Many businesses overlook or underinvest in managed detection and response (MDR), a critical aspect of...

8x8: Collaboration and AI Take Customer Care to the Next Level
This buyers guide examines the North American contact center market for both premise- and cloud-based...

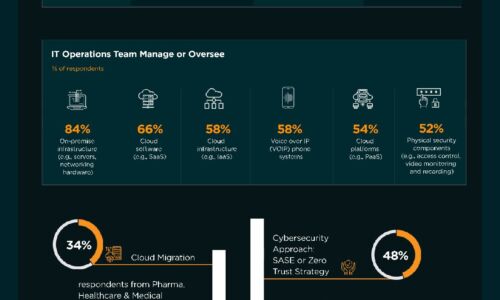
Eight Critical IT Practice Areas That Drive Multi-Cloud Use Maturity
While most organizations are already using two or more clouds, most teams within the larger organization...

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.