VPN

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...
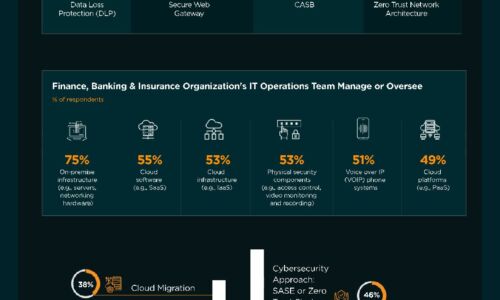
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Zero-trust Solutions for Comprehensive Visibility and Control
Zero-trust solutions exist for nearly every part of the network. However, a piecemeal approach can leave...

3 Ways Emotional Connections Can Power CX
When personalization isn't paying off and data doesn't help you make sound decisions, it's time to renew...

Protecting the ATM Network with Fortinet
Protecting a network of geographically dispersed automated teller machines (ATMs) is a key challenge...

Accelerating Digital Transformation through Hyper-Converged Solutions
How can organizations simplify IT in order to improve business agility, enhance financial return on investment,...

Modern Storage Accelerates Data Insights, Speeding Innovation
Deep learning opens up new worlds of possibility in artifi cial intelligence, enabled by advances in...

Why HIPAA Compliance is Impossible without Privileged Management
Although HIPAA represents only a portion of the total scope of compliance obligations faced by most organizations,...

How Rapac Energy Saves Weeks of Work by Securing Their OT with Cyolo
A leading power plant operator, Rapac Energy, was looking to securely provide access to their OT and...

5 Things You Didn't Know About DDoS Attacks That Can Cost You
To accurately determine your organization's risk of a DDoS attack, you must be aware of the latest trends...

Addressing the Top 10 Security Issues Organizations Face
Cybersecurity must be a top-level priority for any organization and for many it is. Security should be...

Why you need an adaptive security segmentation solution
The threat landscape is more dynamic than ever before, and as business-critical applications traverse...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
