VPN

Cybercrime Tactics and Techniques - Attack on Home Base
The coronavirus pandemic has left the world looking very different at the end of the quarter than it...

The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...

Top 4 Pitfalls to Avoid when Deploying Office 365
There's no denying that Office 365 is a big deal. It's a big part of the Microsoft Intelligent Cloud...

IT’s 5 Toughest Work from Home Challenges and How to Solve Them
2020 forced the shift to a hybrid work model Unexpectedly, you found yourself working from home. The...

IAM for the Real World: Identity Governance
In the real world, governance is a major challenge. In fact, governance can't even be considered until...

5 Steps to Improving Knowledge Management
Advania is an official partner for 4Industry, the digital knowledge management platform for the manufacturing...

It’s 5 Toughest Work from Home Challenges and How To Solve Them
All of a sudden, you (and everyone else) found yourself working from home (WFH). The one advantage was...

Adaptive Multi-Factor Authentication
This white paper provides an overview of Okta Adaptive Multi-factor Authentication (MFA). For security...

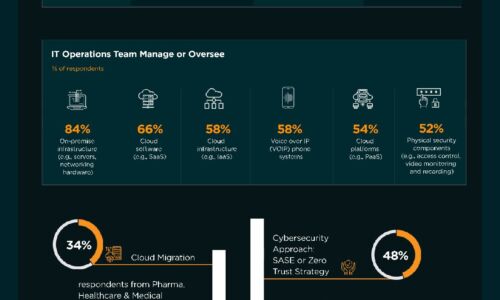
Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.