Latest Whitepapers

Build better endpoint security to protect your entire network
The threat of a serious cyberattack is nothing new — but the situation just keeps getting more complex....

How to Test and Debug Your Mobile Apps in the Cloud
In a heavily fragmented mobile environment, developing applications, which are compatible with multiple...

The CISO's Guide to Ransomware Prevention
Ransomware attacks have transformed the cyber attack landscape. These sophisticated and persistent threats...

Human Potential: Unlocked
Find solutions to the problems that matter to you, the CHRO. Managing risk, increasing revenue, boosting...

Designing Hyper-Aware Industrial Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...

Building Your MSP Security Offerings
As a managed service provider (MSP), your customers already expect you to keep their networks secure....

Book of Knowledge for Customer Experience
Technology is always evolving, and customer expectations are evolving with it. ServiceNow is helping...
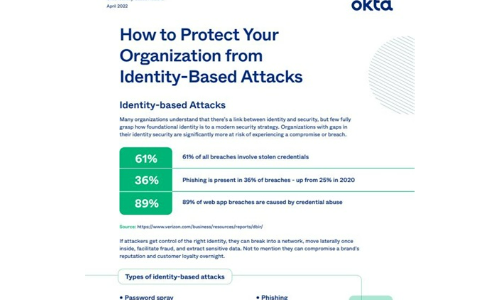
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Artificial Intelligence: The Smarter Approach To Information Security
The news headlines are replete with stories of devastating data breaches, compromising the personal and...

7 Machine Learning Use Cases
Businesses have the opportunity to unlock significant value across the organization with the help of...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









