Endpoint Security

Critical Event Management
For today's organizations, the threat of disruptions that critically impact people and business is unavoidable....

The PC Lifecycle Continuum: From Control to Transformation
As diverse organizations seek to implement data-driven strategies, the personal computer in all its varieties...

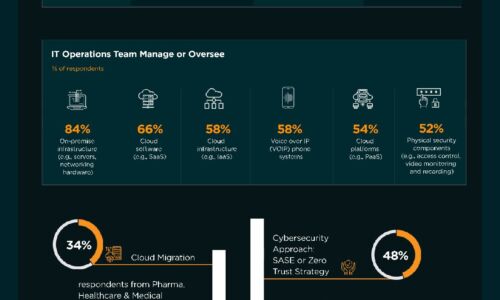
Top 3 Challenges Your Team Faces When Building in the Cloud
Today's cloud and security teams are asked to do more with less. Although the capabilities and cost of...

Forrester Total Economic Impact of Tanium
The Forrester Consulting Total Economic Impact™ (TEI) study commissioned by Tanium helps technology...

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

G2 Mid-Market Endpoint Protection Suites Report
Thinking about investing in endpoint protection and want to get a real sense of how different solutions...

Executive Brief: The Ransoming Of Higher Education
Coordinated attacks are hitting higher education institutions across the nation and around the world....
Responding Smarter, Faster and Better
In cybersecurity, a critical event is a major incident that's disruptive enough to pose a meaningful...

Replace AV Buyer’s Guide
Today's businesses face a unique set of security challenges. Many organizations know their current antivirus...

Security Strategy Checklist
This self-assessment is designed to help you evaluate the security risks in your environment. It is intended...

How to chose a managed extended detection and response solution
Managed Detection and Response (MDR) solutions are specialized security services that allow an organization...

Networking and Information Systems (NIS) Directive
The NIS Directive has been designed to work alongside data protection legislation. It will be governed...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.