Cloud Computing

Protect your Data and Secure your SQL Server Database Operations
You manage hundreds of SQL Server databases spread over multiple sites and departments, even as you face...

How to Build Your Microsegmentation Strategy in 5 Steps
A breach to your organization's network is not a question of if, but when. Are you prepared with a micro-segmentation...
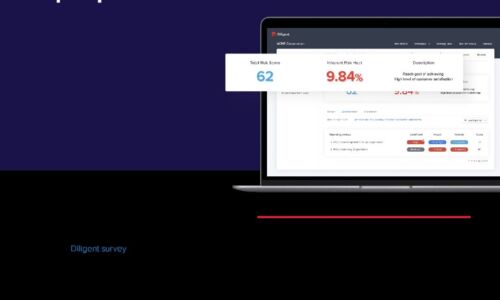
Effective CISO Presentations to the Board: Top Tips & Checklist
As a CISO, you have crucial info to convey about cyber risk, and your board wants to hear it. In a recent...

Zero-Trust is the Outcome of Identity-Based Access Control
As the IT landscape evolves, new and more sophisticated cybersecurity threats continue to appear. These...

DataOps: Moving Financial Services Organizations Into The New Economy
There has never been a more uncertain—yet more promising—time for financial services organizations. Global...

A Change of Pace in IT Transformation
How do your customers expect to interact with you today? What do employees need to connect with each...

The State of Systems of Agreement 2020
All business processes rely on agreements — whether those are agreements between business units, clients,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.






