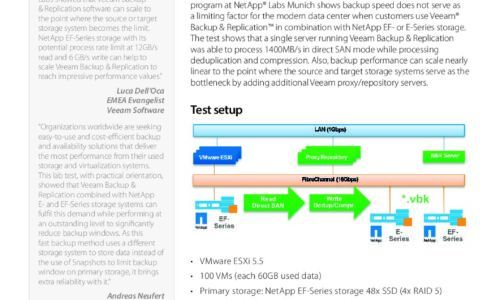
Backups

Farewell ISDN. Hello All-IP.
Analogue and ISDN telephony is a thing of the past – telephony today is mostly internet-based. Voice-over-IP...

Upgrade to State-of-the-Art Log Management
Most log messages traditionally come from three types: system logs of servers, network devices, and applications....

Slash Cloud Backup Costs with Quest QoreStor
Object storage, often referred to as object-based storage, is a data storage architecture for handling...

A Zombie's Survival Guide in a Changing Database World
With the rise of autonomous databases – and all the other scary changes in database management systems...

The Gorilla Guide to Rapid Restores with Flash and Cloud
Welcome to this Gorilla Guide covering enterprise data protection, backup, and recovery. The purpose...

Enterprise Backup and Recovery Made Easy
Protecting enterprise data in a complex IT environment is challenging, time-consuming, cumbersome and...

MandA IT Integration Checklist: Active Directory
If your organization is involved in a merger and acquisition, the impending IT integration project might...

Best Practices for Database Consolidation
Information Technology (IT) organizations are under pressure to manage costs, increase agility, ensure...

Cyber Attack Trends: Check Point's 2022 Mid-Year Report
The war in Ukraine has dominated the headlines in the first half of 2022 and we can only hope that it...

7 Critical Reasons for Office 365 Backup
You have one more reason added to the 6 critical reasons to protect your Office 365 data. This 5-minute...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.