Apple

Ensuring compliant communications in Financial Services
The pandemic has reshaped business in myriad ways, none so much as how people communicate. In a few months,...
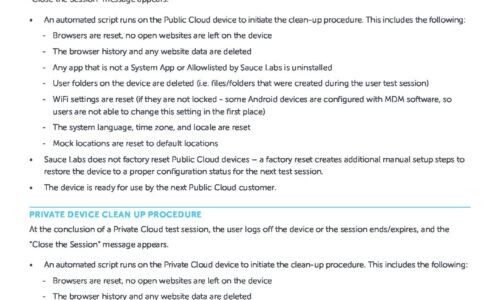
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

A Simpler, Smarter Approach to Mac Management
Mac devices are making massive inroads across every industry, as more companies offer Mac as a choice....

Making hybrid work, work for you
In March 2020, the COVID-19 pandemic forced companies and organizations around the world to shut their...

The Ultimate CX Agent Guide
Customers have embraced technology to manage all aspects of daily lives, setting off a digital disruption...

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...

The US Customer Experience Decision-Makers’ Guide 2019-20
The US Customer Experience Decision-Makers' Guide is a major annual report studying the CX strategy,...

IT and Cyber Incident Response Communication Templates
BlackBerry® Alert is a critical event management (CEM) solution designed to help organizations prepare...

Two-Factor Authentication Evaluation Guide
In this guide, you will learn how to evaluate a solution based on: ...

10 hot-button CX topics for financial services businesses
Learn how to break down silos and unify objectives to lay the foundation for sophisticated omnichannel...

The Anatomy of Account Takeover Attacks
Bad bots are on every website with a login page. Even yours. Hackers and fraudsters use bots to validate...

Evolving From Operating IT To Orchestrating IT
Organisations realise the time is now to move to a new deployment model. Digital transformation and proliferation...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

