Latest Whitepapers

Risk-Adaptive Data Security: The Behavior-Based Approach
This eBook addresses the challenge with DLP of either applying restrictive policies which slow down the...

Security Strategy Checklist
This self-assessment is designed to help you evaluate the security risks in your environment. It is intended...

Effective License Management With A Changing Remote Workforce
Peter Drucker, one of the most widely known and influential thinkers on management, is credited with...

Effieciency, Productivity and Growth - Quickbooks Vs NetSuite
Why stay with software that holds your business back when you could use a system that empowers your business? Improve...

The Future of Retail is Conversations
Retail may never be the same. Consumers who were previously averse to online shopping suddenly embraced...

Analyzing the Economic Benefits of Gigamon
This ESG Economic Validation is focused on the changes companies can expect when deploying Gigamon's...
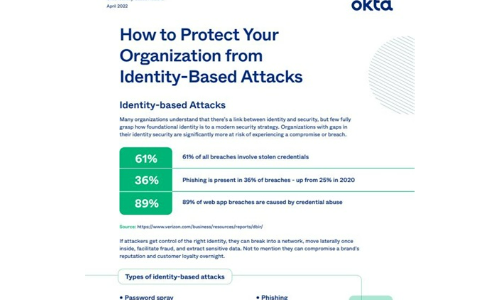
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

How Cloudflare Access Replaces a VPN
The rise of remote work has caught many companies off guard. Many organizations have only purchased enough...

Four Key Considerations for Building the Best Multicloud Architecture
As cloud architects move more workloads to public and private clouds, hybrid multicloud architectures...

97% of data sits unused by organisations
Data has the capability to transform your business, but only if it's collected and processed in the right...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.









