Latest Whitepapers

The Ponemon 2021 Cost of Phishing Study
The financial effects of phishing attacks have soared as organisations shift to remote and hybrid work....

VMware Multi-Cloud Architecture - Enabling Choice & Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

Ransomware Protection Checklist
Ransomware attackers are increasingly employing more sophisticated attacks and defeating existing defenses....
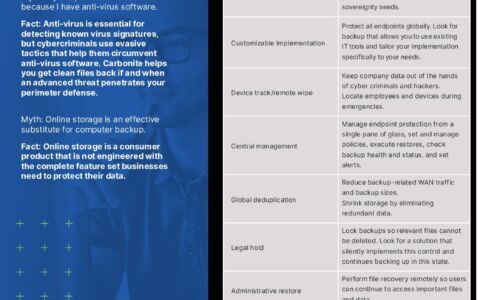
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

Inside HPC: HPC and AI for the Era of Genomics
2020 will be remembered for the outbreak of the Novel Coronavirus or COVID-19. While infection rates...

Know Your Options Before Moving To The Cloud
It's imperative for company and IT leaders to understand that the term 'cloud' is very broad and can...

IDC: Strategies for Building Digital Infrastructure Resiliency
Multiple generations of applications. Multiple generations of infrastructure. Is there a way to reduce...

Security's Privilege Crisis
Despite spending $114B on cybersecurity in 2018, the onslaught of security breaches continues unabated.1...

2022 Annual State of Phishing Report
Enriched with robust threat intelligence from the Cofense Phishing Defense Center (PDC), which analyzes...

Modernizing Your Data Center Is Your Ideal ‘Next' Move
Traditional enterprise infrastructure is under tremendous pressure to deliver far more than it was designed...

How Strategic Automation Drives Crucial Employee Empowerment
With talent shortages set to impact 90% of organisations globally by 2025, automation isn't just a win...

The 12 Essential Elements of Data Center Facility Operations
70% of data center outages are directly attributable to human error according to the Uptime Institute's...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.







