Virtualization

Three reasons to manage Office 365 with Citrix Workspace
Are you considering migrating to Microsoft Office 365 or already facing challenges with the move? Don't...

Protect K-12 Schools from Cyberattacks with Active Breach Protection
Ransomware is not just another buzzword. It is a very real threat to educational institutions of all...

ServiceNow + Vonage: The Perfect Combo
Video Overview of Vonage Contact Center and ServiceNow - Vonage Contact Center (VCC) for ServiceNow integrates...
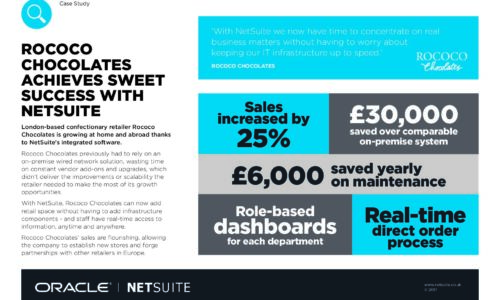
Rococo chocolates achieves sweet success with NetSuite
London-based confectionary retailer Rococo Chocolates is growing at home and abroad thanks to NetSuite's...

Business Growth and Agility in the Cloud - Infor vs NetSuite
If you want to go further, grow faster and achieve more than your competitors, you need to have the right...

Multi-cloud Load Balancing for Dummies
Legacy hardware-based load balancers don't meet modern enterprise application delivery requirements in...

Modernizing Your Data Center Is Your Ideal ‘Next' Move
Traditional enterprise infrastructure is under tremendous pressure to deliver far more than it was designed...

Edging Towards SASE: Next generation networking, cloud and security
The global pandemic has delivered a paradigm shift in the relationship between employees and their workplace. The...

Understanding Log Analytics at Scale
The humble machine log has been with us for many technology generations. The data that makes up these...

A Smarter Contact Centre for Employee and Customer Experience
For years, customer service has prioritized cost containment and contact deflection. Today, rising customer...

Security Starts Here: Privileged Access Management
The threat of a security incident or critical error is very real, and it's something that auditors are...

Cybersecurity For Dummies
Advanced threats have changed the world of enterprise security and how organizations are attacked. These...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
