Storage
Tracking Bot Trends for first half 2020
Recent bot trends you need to know: Bots can harm an Internet property in a variety of ways and cause...

5-minute Primer: MultiLine at Work
What do you do when your employees conduct company business on their personal devices? On one hand, it...

Decrease Downtime and Increase Efficiency, Collaboration and Profitability
Across the State of Qatar – in football stadia and landmark buildings, on highways and critical infrastructure...

Breaking Down Walls With Digital Technology
The diversity and bureaucratic nature of government agencies have complicated communication for decades....

A hybrid vision for the new era of digital transformation
If you are embarking on your digital transformation journey with cloud being an integral part, the best...

Application Protection Report 2022: In Expectation of Exfiltration
Welcome to F5 Labs' Application Protection Report 2022. As in years past, the goal of this report is...

Networking and Information Systems (NIS) Directive
The NIS Directive has been designed to work alongside data protection legislation. It will be governed...

Tintri Introduces SQL Integrated Storage
What is SQL Integrated Storage? A SQL database is, essentially, a collection of files with associated...

How SD-WAN Supports Digital Transformation in Healthcare
Advancements in medicine, the increase in regulations to protect patient and doctor, and the digitization...

Innovating in the Exponential Economy: Chapter 2
For all businesses, innovation is crucial for competitiveness and survival but it is notoriously hard...
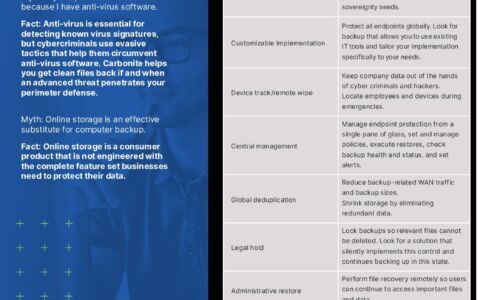
Carbonite Endpoint Protection Myths
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


