Storage Devices

Unlocking collaboration in higher education
Collaboration and knowledge sharing are pillars of higher education. Instead of working in silos detached...

Cyber Security for Dummies
Protect your business and family against cyber attacks Cybersecurity is the protection against the unauthorized...

All-Flash Buyer's Guide: Tips for Evaluating Solid-State Arrays
Think Flash-First for Primary Storage. The introduction of enterprise-grade all-flash arrays has turned...

Sophos 2022 Threat Report
Interrelated threats target an interdependent world. We believe that shifting the timescale of attack...

Ponemon Cost of Insider Threats Report 2022
External attackers aren't the only threats modern organisations need to consider in their cybersecurity...

Solve the security puzzle with end-to-end security solutions
As an IT decision maker, you're focused on finding effective solutions you can implement quickly and...

CISSP For Dummies
Secure your CISSP certification! If you're a security professional seeking your CISSP certification,...

Ransomware Threat Briefing
Cyber criminals are getting bolder and more sophisticated with their threats. No matter what kind of...

Ransomware Prevention Is Possible
Ransomware is a form of malware that encrypts files to prevent victims from accessing their systems and...

An introduction to ITM
As organisations move towards a more distributed workforce, the traditional perimeter of the office network...

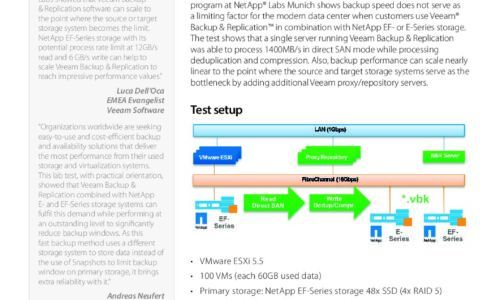
How to Build a Lightning- Fast, Multi-Petabyte Backup Repository
IT teams are facing exponential data growth. It's natural to worry about exceeding capacity, wondering...

Modern Blueprint to Insider Threat Management
Taking a People-Centric Approach to Your Insider Threat Management (ITM) Programme. Insider threats can...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.