Software

IDC white paper security
The business criticality and cyber-risk of endpoint devices could not be greater. With the COVID-19 pandemic,...

Evaluating Modern Enterprise Storage
Rapid data growth and proliferating strategic digital business initiatives have been transforming organizations....

Evolution Of The Marketer's Toolkit
More than ever, enterprise organisations need a 360-degree view of their customers to deliver the kind...

The Top 10 Reasons to Upgrade to VMware vSphere 7
Customers today demand rapid delivery of innovative applications. To meet those demands, businesses must...

Understanding Augmented and Virtual Reality
In the book, A Whole New Mind: Why Right-Brainers Will Rule the Future, author Daniel Pink describes...

The Economics of Cloud Options in Healthcare
Through the lens of Cloud Economics, explore the risks and benefits of the three ways to upgrade and...

Six Steps to Successful and Efficient Threat Hunting
Rather than waiting for an alert, threat hunters proactively assume that an advanced adversary operates...
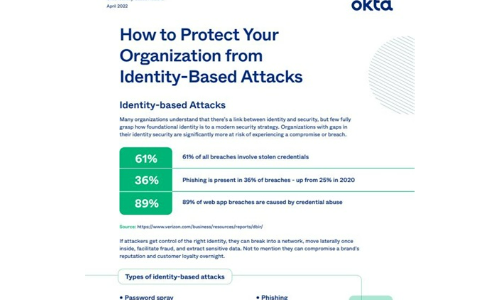
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

DEIB Analytics: A Guide to Why & How to Get Started
Gain insights from RedThread Research on why businesses are focused on diversity, equity, inclusion and...

Insider Threat Prevention Guide
In a perfect world, trust would never be violated. Cyber defenses would be impregnable. No employee would...

VMware NSX Advanced Load Balancer Benchmark Report
Moving from appliance-based load balancers to software-defined VMware NSX Advanced Load Balancers could...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


