Server

2 Steps to Achieve Endpoint Compliance with KACE® by Quest
Next to ongoing security issues, meeting compliance mandates is one of the biggest challenges IT professionals...

The Definitive Guide To SASE
What is Secure Access Service Edge (SASE) and why do you need it? Download the new guide to learn how...

Getting to digital experience excellence
With our Digital Acceleration program, you'll work with Adobe strategy consultants to uncover KPIs and...

Protecting Your Hybrid and Hyperscale Data Centers
Organizations are building hybrid data centers that consist of composable and scalable architectures....

The Anatomy of an Insider Threat Investigation
For decades, perimeter-based security strategies have been the starting point for most cybersecurity...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...

How Intrinsic Security Protects Against Business Disruption
When it comes to IT, disruption is just another day at the office. From fending off cyberattacks to incorporating...

The strategic ROI of network management
ROI for all forms of integrated DNS, DHCP and IP Address Management (DDI) solutions is largely comprised...
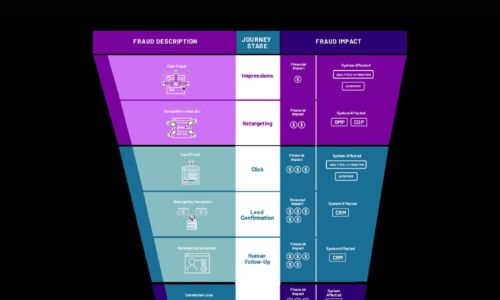
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

Security Control Guide: Hardened Services Guide
System Hardening is the process of securing a system's configuration and settings to reduce IT vulnerability...

7 Leading Machine Learning Use Cases
Machine learning drives results While machine learning has moved beyond the hype to become a meaningful...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


