SASE

SASE-Ready WAN Edge for the Work from Anywhere Era
Enterprise networks are on the verge of a major tipping point, driven by the shift from employees working...

Proofpoint Information and Cloud Security Platform
The Proofpoint Information and Cloud Security platform combines many of our products to address secure...

Can ZTNA replace your VPN?
Compare 3 remote access approaches Seamless remote access enables companies to boost employee productivity...

Verizon and Palo Alto Networks Enabling a Secure Connected World
Supporting mobility, minimizing the attack surface, and having reliable access to applications are key...

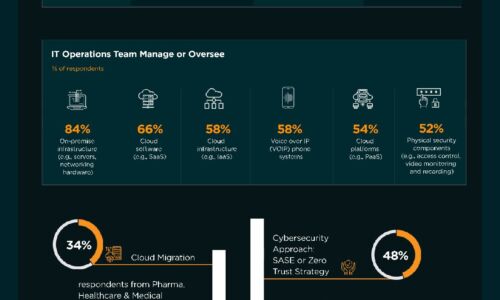
The State of SD-WAN, SASE and Zero Trust Security Architectures
The purpose of this research is to learn important information about the use of Software-defined Networking...

Office of the CTO Report: Continuous API Sprawl
APIs are a contract between the service provider and service consumer. When any application uses an API,...

Getting Started with SASE
Secure Access Service Edge: A guide to secure and streamline your network infrastructure As enterprises...

Cloud Data Security 2023 Report by ESG, a division of TechTarget
…More than half (59%) of respondents believe that more than 30% of their organization's sensitive data...

Your Path to Zero Trust
In a business world without perimeters and dominated by remote work, finding a balance between easy collaboration...

Protecting Every Edge To Make Hackers' Jobs Harder, Not Yours
Today's users need a network that allows them to connect to any resource from any location using any...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.