SAN

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...

The New Era of Fraud: An Automated Threat
Fraudsters employ bots and automated attacks that scour apps looking for any opportunity to hijack business...

Practical Guide To A Zero Trust Implementation
Zero Trust is becoming the security model of choice for enterprises and governments alike. However, security...

Comparing AWS Tools for Cloud Cost Management and Optimisation
Cloud cost management and optimization can become a big challenge as organizations find that the decentralized...
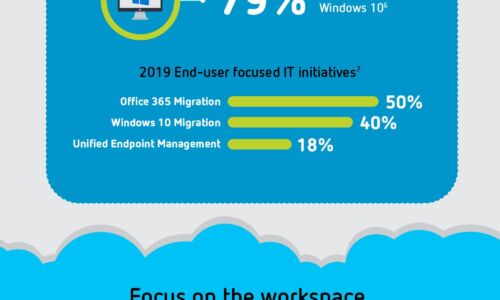
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

5 Benefits of Partnering with Webroot
While cyberattacks continue to evolve in volume, organization, and sophistication, security technology...

No Going back? The UK’s Irreversible Work / Life Shift
The urgency created by events in 2020 acted as a catalyst to faster executive decision-making and action....

AWS for Healthcare: Accelerating the Future of Personalized Healthcare
For healthcare organizations, the challenge of providing patient centered care amid ever-increasing costs...

Human Factor Report 2021
Cybersecurity, Ransomware and Email Fraud in a Year that Changed the World As the global pandemic upended...

An introduction to ITM
As organisations move towards a more distributed workforce, the traditional perimeter of the office network...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

The SMB Opportunity for MSPs: 2021-2026
According to new research from ConnectWise, MSP industry trends show that SMBs will create over $90 billion...

11 Recommended Security Practices to Manage the Container Lifecycle
This paper details 11 recommended practices for DevSecOps teams needing to move to a more modern application...

Find and Protect Your Sensitive Data with SQL Server Compliance Tools
This technical brief examines a database compliance and security scenario in the enterprise. It describes...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.