SAN

Data Reinvention: Business Transformation Through a New Lens
This HBR Report explores the value that data is bringing to organizations and how to avoid the common...

Five Lessons Learned from the Pivot to a Distributed Workforce
Today, it is increasingly important to enable your employees to work remotely. Working remotely gives...

Ransomware Prevention Is Possible
Ransomware is a form of malware that encrypts files to prevent victims from accessing their systems and...

Zero Trust Access for Dummies
As businesses continue to embrace digital innovation, cloud applications, and the new work-from-anywhere...

VMware Multi-Cloud Architecture - Enabling Choice and Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

Modern infrastructure for better end user experiences
Many companies with existing EUC deployments are refreshing their technology stacks to deliver a better...

Overcome Database Indexing Challenges
Overcome your database indexing challenges – read this MSSQLTips white paper today By properly using...

Moor Insights: Cloud is Built on Modern Infrastructure
The modern enterprise lives in a multi-cloud world, where delivery of infrastructure resources and IT...

Architecting the Zero Trust Enterprise
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit...

The AI & Machine Learning Imperative
Companies across various industries are seeking to integrate AI & machine learning (ML) into workflows...
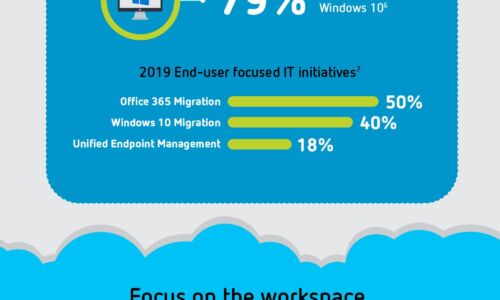
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

VMware Multi-Cloud Architecture: Enabling Choice and Flexibility
In today's world, application growth is unprecedented and enterprise applications on a wide range of...

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...

Instant data for real-time business results
Machine learning is evolving faster than ever – AI and analytics can give you the capabilities to become...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.