Network

Go Mainstream with SD-WAN: Migration Best Practices
Over the last couple of years, SD-WAN technology has matured into a mainstream solution. Yet, the most...

The Definitive Email Cybersecurity Strategy Guide
Email is your most essential business tool—and today's top malware delivery vector. This vital communications...

Enduring from Home: COVID-19's Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

Reinventing work How leading
We're coming off one of the most challenging years in business history. The pandemic forced every company...

Security's Privilege Crisis
Despite spending $114B on cybersecurity in 2018, the onslaught of security breaches continues unabated.1...

Enterprise-Wide Network Segmentation
The promise of digital transformation efficiencies, innovation and productivity has resulted in flat,...

Organizations Accelerating Their Digital Workplace Achieve Improvements
This study sought to understand whether, and to what degree, an organization's adoption of modern device...

Multi-Vector Protection
Educating users is an undeniably effective way to protect them from phishing and other malware, but it...
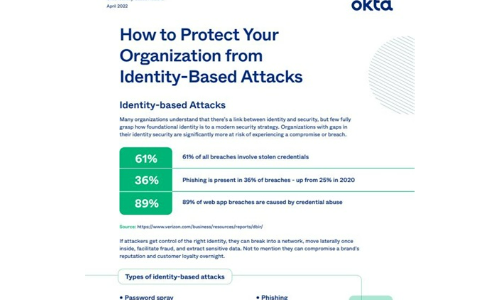
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...

Progressive CIOs: driving finance transformation
A successful finance transformation requires several ingredients: vision, agility, and the right system...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



