Network

Defend Against Ransomware
Defend your organization from evolving ransomware attacks. Learn what it takes to reduce risk and strengthen...

Understanding Log Analytics at Scale
The humble machine log has been with us for many technology generations. The data that makes up these...

The 7 Hidden Truths of Cloud Security
Based on extensive, up-to-date knowledge and experience from WithSecure consultants, threat hunters and...

Defend Yourself Against Ransomware and Other Types of Malware
The May 7, 2021, ransomware attack on U.S. fuel network Colonial Pipeline left millions afraid they couldn't...

Slash Cloud Backup Costs with Quest QoreStor
Object storage, often referred to as object-based storage, is a data storage architecture for handling...
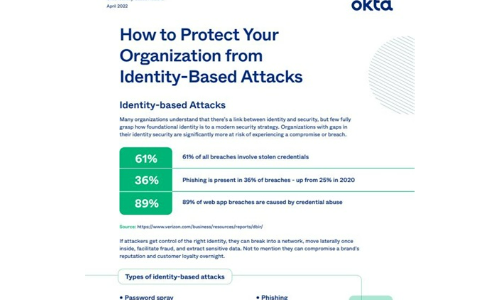
How to Protect Your Organisation from Identity-Based Attacks
Many organizations understand that there's a link between identity and security, but few fully grasp...
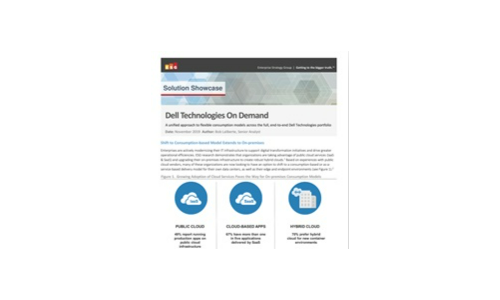
ESG: Dell Technologies on Demand
Enterprises are actively modernizing their IT infrastructure to support digital transformation initiatives...

Go Mainstream with SD-WAN: Migration Best Practices
Over the last couple of years, SD-WAN technology has matured into a mainstream solution. Yet, the most...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.





