Network Security

Learn How to Build Resilient Global Applications
Quick 5 minute read! Deliver high performance and always-on applications anywhere with Active-Active. Today's...

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

The Total Economic Impact™ Of The CB Predictive Security Cloud
Your endpoints are one of the most targeted assets in your organisation. In 2017 alone, more than 50%...

CompTIA A+ Certification All-in-One For Dummies, 5th Edition
Fully updated to cover the 2019 exam release! CompTIA's A+ certification is an essential certification...

Four Data & Analytics Trends to Watch in 2020
The buzz around headline-grabbing topics like machine learning (ML) and artificial intelligence (AI)...

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...

Elastic Cloud Gateways: The Evolution of Secure Cloud Access
Enterprise security groups today face a daunting task. While their core responsibility of protecting...

A Guide to Assessing Security Maturity
Cybersecurity is an unavoidable part of daily business operations for organizations of all sizes and...
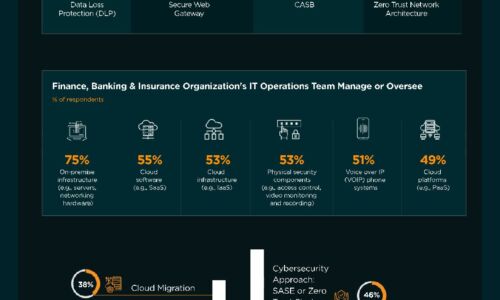
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Insider’s Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

The State of Threat Prevention: Evasive threats take Center Stage
Digital transformation has rendered many traditional security solutions useless in the face of modern...

Network Security that sets the standard for local government
When it comes to network security, organisations can — and must — learn from the experiences of others....

Python for Data Science For Dummies, 2nd Edition
The fast and easy way to learn Python programming and statistics Python For Data Science For Dummies...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
