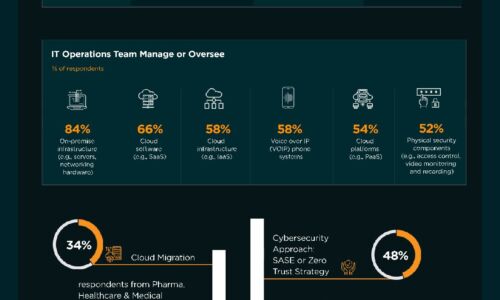
Network Security

8 Ways To Evaluate An MDR Provider
For many organizations, digital transformation had been a business initiative for years, but the pandemic...
Finding a Setting Worthy of Your “Crown Jewels”
Keep all the Data in a single, unified Database – Oracle Exadata For most companies, data is critical...

IT’s 5 Toughest Work from Home Challenges and How to Solve Them
2020 forced the shift to a hybrid work model Unexpectedly, you found yourself working from home. The...

Application security, fallacies + realities
The news headlines have been filled with stories about security breaches in recent months. And most of...

Transforming Security in the Mobile Cloud Era
In the age of digital transformation, maintaining secure interactions among users, applications, and...

A Buyer's Guide to Optimizing Remote Employees' Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...

How to Get and Maintain Control of Your Microservices
Learn how a hybrid application delivery system powered by Citrix ADC can help you gain control of your...

Consolidate Cybersecurity Vendors to Accelerate Detection and Response
Organizations of all shapes and sizes are increasingly embracing digital transformation, cloud-delivered...

Cloud networks: Shifting into Hyperdrive
Public cloud is driving digital innovation. As IT organizations around the world continue to radically...

State of Digital Transformation EMEA 2020
Prior to the pandemic, enterprises were actively migrating private applications to public clouds as well...

Get a Fast Office 365 User Experience
Recommendations for a smooth migration, fast results. A Microsoft Office 365 migration can be daunting....
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.