Mobile Security

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...
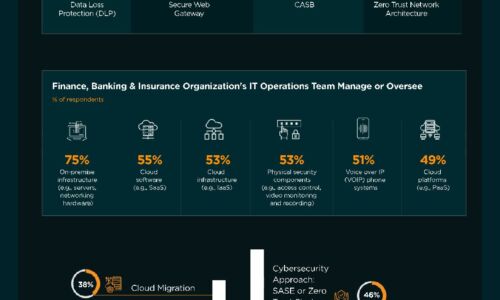
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Python for Data Science For Dummies, 2nd Edition
The fast and easy way to learn Python programming and statistics Python For Data Science For Dummies...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.
[mc4wp_form id="461" element_id="style-9"]