Malware

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...
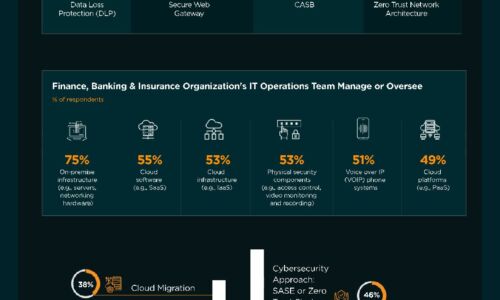
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Enhancing Microsoft Security with HelpSystems Email Security
Learn how HelpSystems Email Security can enhance Microsoft 365. Microsoft 365 offers tiers of security...

How to Deploy a Comprehensive DevSecOps Solution
Securing DevOps is a complex undertaking, DevOps tools grow and change at a fast pace. Containers and...

How to chose a managed extended detection and response solution
Managed Detection and Response (MDR) solutions are specialized security services that allow an organization...

Cloud Usage in the Financial Services Sector
This survey was created and completed by members of the the Financial Services Stakeholders Platform,...

Challenging Times Call for a Cybersecurity Plan of Action
Could there be a more 'exciting' time to be a cybersecurity executive? Some might choose other adjectives:...

Tanium Insights: It's Time to Ditch the VPN for Zero Trust
Many organizations have started adopting zero trust strategies to protect their distributed networks...

A Visual Landscape Of Cybersecurity
Our world has never moved faster in terms of cyber threats, security technology innovations and overall...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




