Laptops

Trusted Access Report
As global conflicts spill into the digital realm, protecting people through to the enterprise is increasingly...

Windows Server 2019 and PowerShell All-in-One For Dummies
Windows Server 2019 and PowerShell All-in-One For Dummies offers a single reference to help you build...

Build better endpoint security to protect your entire network
The threat of a serious cyberattack is nothing new — but the situation just keeps getting more complex....
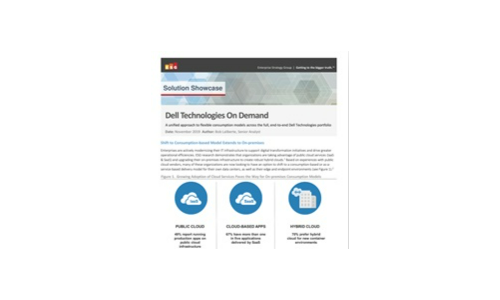
ESG: Dell Technologies on Demand
Enterprises are actively modernizing their IT infrastructure to support digital transformation initiatives...

Modernize the workforce experience
It's more than a concept, it's our approach to modernizing your workforce. Our products, solutions and...

Software Testing in a Post Pandemic World
Sauce Labs offers the broadest mobile testing solution in the industry to help modern mobile development...

The Future Of Enterprise Computing Starts Now
Gone are the days when IT operated in a dark, back-office environment, where they had little to no impact...

Meeting Man Group's Security Needs with Slack Enterprise Grid
Learn how a global investment firm of 1,400 employees made an immediate transition in response to Covid-19. This...

Ransomware Case Studies
Ransomware is a simple name for a complex collection of security threats. Attacks can be short and brutal,...

10 Security Tips for Businesses
SECURITY THAT PROTECTS YOUR BUDGET Vanishing budgets, reckless users, infected machines, unpatched software...

BlackBerry Cyber Suite
The challenge of securing and protecting data and endpoints is not a new requirement, but today it is...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


