IT Threats & Vulnerabilities

Why Corelight Is Your Best Next Move In Enterprise Security.
Despite spending billions annually on security infrastructure and services, even the most sophisticated...

Chart Industries vaporizes ransomware and malware
Malwarebytes enables IT to shift its focus to strategic security project work. The company in this case...

Use Case-Driven Cloud Security Evaluator Guide
Researching cloud security? Be sure you evaluate yourself and your vendors on the 6 most common cloud...

Shift your Web Security to the Cloud, for the Cloud
As enterprises embrace digital transformation, the adoption of software-as-a-service (SaaS) is robust...

Legal Practice in a Hyper-Connected World
Essential Capabilities and Branding for the New Digital Client. Technology is changing the way that businesses...

Top 5 Ways to Simplify Data Protection with Microsoft Azure
Read this white paper to find out five ways that you can simplify data protection with Microsoft Azure,...

Is Your WAF Keeping Pace with Today's Advanced Threats eBook
As the threat landscape evolves, so must our security controls and countermeasures. Recent research from...

Privileged Access and the Impact of Pass the Hash Attacks
The goal of this survey was to capture hard data on current experiences, trends and approaches to Identity...

The Survivor's Guide to Building an Office 365 Network
A Microsoft Office 365 deployment can be daunting. From a fast user experience, to a cost-cutting productivity...
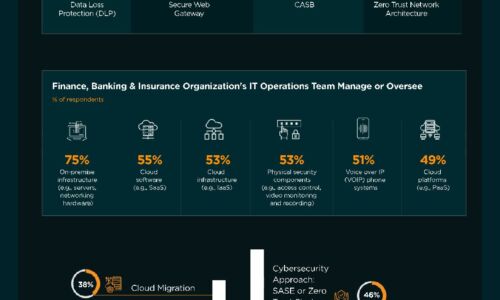
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

From Seismic Disruption to a New Era of Success
No one could have foreseen the terrible impact of the COVID-19 outbreak on humankind. In business too,...

Securing Cloud Transformation with a Zero Trust Approach
When it comes to rates of change, cybersecurity has rightly been on the conservative side. Setting up...

The Best of Both Worlds: Hybrid IAM Offers Flexibility and Enhanced Security
One of the fastest growing segments of the Identity and Access Management (IAM) market is the cloud segment. Increasingly,...

Optimized Security for Multi-Cloud laaS Environments
No question: Multi-cloud adoption can benefit your business. New question: How can you secure multi-cloud...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.