IT Security

Security Operations Maturity Model
A practical guide to assessing and improving the maturity of your security operations through Threat...

5 Critical Requirements for Internal Firewalling in the Data Center
Preventing hackers from hiding inside large volumes of east-west network traffic has now become critical...

Building A Better Cloud Begins With Better Infrastructure
The modern enterprise lives in a multi-cloud world, where delivery of infrastructure resources and IT...
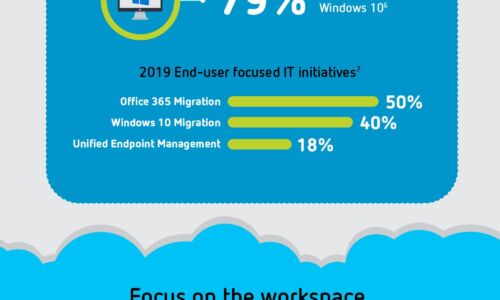
Digital Transformation: A Look Ahead
Digital transformation is reshaping organizations into digital businesses. Organizations are focused...

Why Today's Business Applications Belong in the Cloud
Has there been a more exciting time to be at the forefront of business? It's unlikely. According to a...

Mobilising employee productivity in the distributed workplace
Citrix and Microsoft shape modern workplaces that unite the essential elements of today's distributed...

5 Myths about Privileged Access Security for AWS
In today's modern enterprise, more companies rely on an IaaS model. In fact, 93% of IT decision makers...

VMware Cloud Workload Migration Tools
Before starting a cloud migration project, it is critical to understand the strategies and tools available...

Advanced MySQL 8
Design cost-efficient database solutions, scale enterprise operations and reduce overhead business costs...

3 Ways to Make Cloud your Business eBook
The role of IT infrastructure and operations leaders has dramatically changed, and cloud evolution continues...

Filling the Gaps in Office 365
Office 365 offers a variety of choices and added functionality making it confusing for IT teams to decide...

GigaOm Radar for Phishing Prevention and Detection
Get your complimentary copy of this independent GigaOm Research report, which analyzes positioning and...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

