Firewall

Securing Microsoft 365 with Fortinet Security Fabric
The Fortinet Security Fabric provides broad, integrated, and automated protection across the organization—on-premises,...

Citrix SD-WAN for Azure Virtual WAN
A partnership that puts you first. Citrix is a Microsoft Virtual WAN preferred partner. This means that...

2022 Social Engineering Report
In our latest social engineering report, Proofpoint researchers analyse key trends and behaviours in...

Rackspace Fanatical Support for AWS
As organizations move their workloads from traditional data centers to AWS, IT security paradigms are...

Python for Data Science For Dummies, 2nd Edition
The fast and easy way to learn Python programming and statistics Python For Data Science For Dummies...

OutSystems for Digital Banking
Create a Frictionless Digital Banking Experience With the Power of Low-Code The retail banking industry...

Oracle NetSuite Protects Flagship Business Applications With Illumio
Find out how SaaS leader Oracle NetSuite improves security and uptime for 7,500 application workloads...

Database Solutions Pocket Book
Given the fast pace of modern business, traditional enterprise infrastructure is ill-suited to meet the...
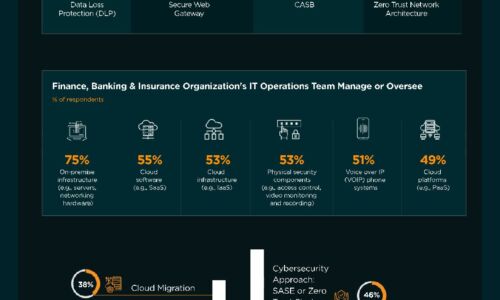
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

A Buyer’s Guide to Optimizing Remote Employees’ Extended Network
The shelter-in-place mandates put in place earlier in 2020 sent most employees home, and for the next...

Nasuni for Rapid Ransomware Recovery
The FBI's Cyber Crime division defines ransomware as 'an insidious type of malware that encrypts, or...

7 Reasons VMware Cloud Foundation is the Premier Hybrid Cloud Solution
Is your IT service delivery future ready? Application and cloud strategies are inextricably linked, and...

Dissecting a Cloud Attack: Securing Azure with AzLog
Microsoft Azure is one of the fastest-growing cloud infrastructure services. Unfortunately, the advantages...

The Definitive Guide to SharePoint Migration Planning
Getting your SharePoint migration right is essential to a host of important goals, from business continuity...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.