Event Management

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...
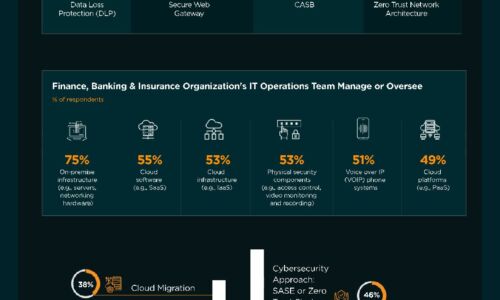
Finance, Banking & Insurance Industry | State of Cybersecurity 2021
This infographic by ISACA and HCL Technologies discusses the state of cybersecurity within the finance,...

Securely Enabling a Hybrid Cloud in Microsoft Azure
The public cloud has rapidly moved past the novelty, curiosity stage to the business critical initiative...

Veeam Enterprise Availability for SAP HANA
Enterprise-grade companies uses SAP HANA worldwide, this is the application directly related to customers...

CISO’s Playbook to Cloud Security
To secure enterprise assets in the cloud, CISO's must address several new challenges unseen in traditional...

Next-Gen Digital Transformation for Law Firms
Optimize opportunities to grow your practice and mitigate risk. Law firms, like other businesses, have...

Top Workplace Trends 2023 (& Why Communications Are Essential)
What changes are coming for your organization in 2023? Looking ahead is essential for successful businesses....

Telstra's Best Practice Guide to Hybrid Cloud
Hybrid Cloud is becoming the strategy of choice for enterprises that want the best of both public cloud...

The Survivor's Guide to Building an Office 365 Network
A Microsoft Office 365 deployment can be daunting. From a fast user experience, to a cost-cutting productivity...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.




