
Optimizing Workload Placement in Your Hybrid Cloud
Many IT organizations are in the process of modernizing their infrastructure, as part of either a digital...

The Zero Trust Guide To Remote Worker Security
With the recent increase in the number of employees working from home as a result of the COVID-19 outbreak,...

Enduring from Home: COVID-19’s Impact on Business Security
Faced with shelter-in-place orders in their home counties and states, countless companies transitioned...

Designing Hyper-Aware Healthcare Facilities
At its core, the Internet of Things (IoT) is an amalgamation of machines in the physical world, logical...
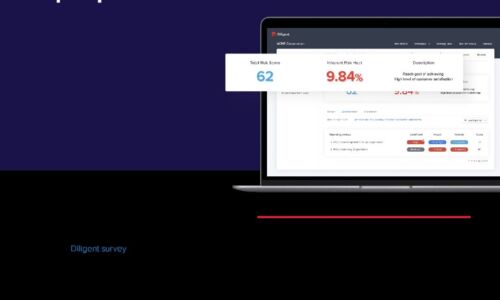
Effective CISO Presentations to the Board: Top Tips & Checklist
As a CISO, you have crucial info to convey about cyber risk, and your board wants to hear it. In a recent...

Drive CPG Revenue through Digitalized B2B E-Commerce Ordering
E-commerce has been shaping buying trends for the past 20 years. But surprisingly, the global B2B e-commerce...

Making the Case for Case Management
It's been nearly two decades since the public sector took that first look into the soul of its customer...

Economist: Signals and Noise: The New Normal in Cybersecurity
Cybersecurity is a top priority for Boards and the C-Suite. Strengthen your security posture with executive...

FOUR COMPLIANCE TRENDS FOR 2021
If 2020 was the year the financial services industry was turned on its head, what's in store for compliance...

Endpoint security versus productivity in utilities: a false choice?
Utility companies are often targeted because they can be used so effectively as phishing lures, as they...

The New Future of Work
To address the challenges of 2020 and emerge stronger in this New Future of Work organisations need to...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


