
The 3-2-1 Data Protection Rule and Hybrid Cloud Backup with NetApp
IT teams are under extreme pressure to improve backup, disaster recovery and data protection to eliminate...

Nylas quickly protects against the Log4j vulnerability using Lacework
Nylas is a communications API platform that helps developers quickly and securely build email, scheduling,...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Part Four- Futureproofing your cybersecurity strategy
Email account takeovers are among the most insidious and damaging cyberattacks—used to invade companies...
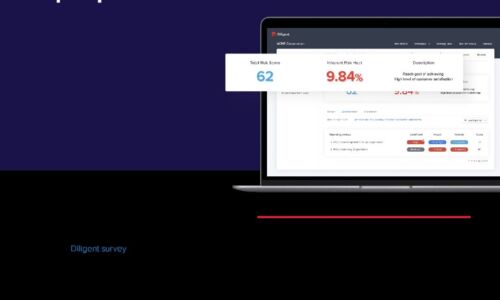
Effective CISO Presentations to the Board: Top Tips & Checklist
As a CISO, you have crucial info to convey about cyber risk, and your board wants to hear it. In a recent...

Insider’s Guide To Choosing a DNS Service
The need that DNS (the domain name system) was created to address seems simple enough: where can I find...

Automation's rising tide: How to manage bots in today's world
Have you ever wished for an army of clones to do all your thankless tasks and chores? Well, that fantasy...

Python All-In-One For Dummies
Your one-stop resource on all things Python! Thanks to its flexibility, Python has grown to become one...

Quest Toad for Oracle Tips and Tricks
Toad® for Oracle has been the IT community's tool of choice for more than a decade. With Toad, you are...

Cybercrime Tactics and Techniques - Attack on Home Base
The coronavirus pandemic has left the world looking very different at the end of the quarter than it...

Spear Phishing: Top Threats and Trends
Cybercriminals are constantly refining their tactics and making their attacks more complicated and difficult...

The Future of Secure Communications
How BlackBerry's SecuSUITE is changing the way governments and enterprises communicate. In an increasingly...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

