Data Center

Learn how to build a business framework designed for data management
The center of a best practice approach must include a complete view into your organization and its technology...

Leadership trends report: operating excellence
Optimising business operations used to mean just lowering costs and increasing profits. But today, you...

A Buyer's Guide to Audit Management Software
For today's internal audit teams, the audits themselves are only one part of a growing scope of responsibilities. Executives...

Reinventing work How leading
We're coming off one of the most challenging years in business history. The pandemic forced every company...

Successful Microsoft Azure Migration with Quest Data Empowerment Tools
What if there was a model for methodically approaching migration of even your most entrenched relational...

A Guide to Assessing Security Maturity
Cybersecurity is an unavoidable part of daily business operations for organizations of all sizes and...

Charting a Course to SAP Modernization Success
As enterprises plan their SAP modernization efforts, they are looking for solutions that allow them to...

Insurance MFA case study – on-premise and multiple integrations
UNIQA Czech Republic is part of one of the leading insurance groups, UNIQA, located in Austria, Central...
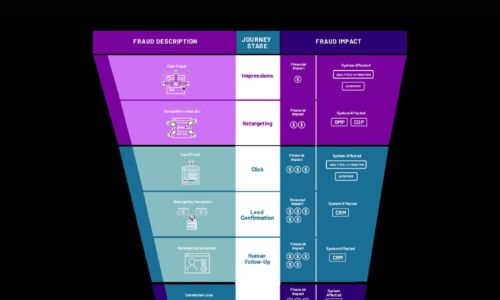
Cybercrime Threatens the Digital Funnel
Cybercriminals are employing new attack methods on new digital surfaces, including digital marketing....

Transform your business with machine learning
8 stories of machine learning success By providing the broadest and most complete set of machine learning...

Learn the 10 questions your cloud partners should be able to answer
Evaluating cloud partners can be overwhelming. These 10 key questions will help find who's best suited...

NIST Cybersecurity Framework
The document gives you an overview of the NIST Cybersecurity framework, an internationally widespread...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.

