Cloud
Carbonite Endpoint Protection Myths
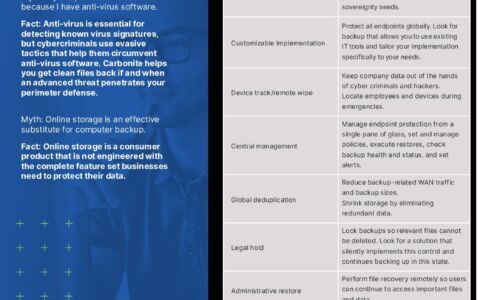
Myth: My endpoint data is secure because I have anti-virus software. Myth: Online storage is an effective...

The Gorilla Guide to Rapid Restores with Flash and Cloud
Welcome to this Gorilla Guide covering enterprise data protection, backup, and recovery. The purpose...

OWASP Top 10
The nonprofit Open Web Application Security Project (OWASP) works to improve the security of software,...

Step-by-step Cloud Evolution with Microsoft Azure
IT transformation is more than a one-time migration of applications to the cloud, it's an ongoing process...

A guide to the benefits of Unified Communications & Collaboration
In order to succeed, modern businesses must seek to create a workplace that delivers an exceptional customer...

Cloudflare Gateway
How do you stop sensitive data from leaving your organization? Traditional approaches to securing employee...

Forrester Consulting Study: Trusting Zero Trust
The growth of ransomware and work-from-anywhere employment has created vastly greater security risks....

Protect and Preserve Your Data from Endpoint to Infrastructure
Technology has made it possible for the world to maintain a somewhat business-as-usual stance, even when...

The AI & Machine Learning Imperative
Companies across various industries are seeking to integrate AI & machine learning (ML) into workflows...

Third-party Risk Management Essentials
From big banks and university hospitals to retail fashion chains and every level of government, organizations...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



