Cloud

How to Test and Debug Your Mobile Apps in the Cloud
In a heavily fragmented mobile environment, developing applications, which are compatible with multiple...

Securely Work From Anywhere With the Fortinet Security Fabric
The way people work has fundamentally evolved, and organizations need to be able to keep workers productive...
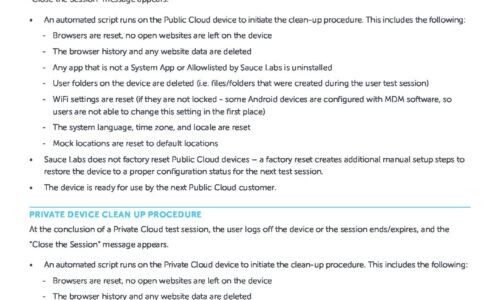
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

Create crucial trust
Learn the unexpected power of connecting operations across the enterprise to seize the upside and mitigate...

CISO's Guide to Third-Party Security Management
Managing your third-party vendors' security is crucial, but security assessments are riddled with problems. Lengthy...
Are you prepared... to reskill and recruit 500 employees?
Discover how a unified system for HCM, finance and planning prepares you to quickly reskill, recruit,...

Leadership trends report: Global app development roadmap 2022-2025
Digital leaders need to keep pace as new technologies are adopted across the enterprise, but today most...

5 New Rules to Protect Your Data Centers and Cloud Environments
In this white paper, we look at five new rules to secure data centers and cloud environments. These rules...

API Testing Automation and Monitoring: Avoid a False Sense of Security
Dive into the stories behind several devastating API bugs that impacted five well-known large enterprises....

Three Reasons to Move from Legacy Data Loss Prevention
Changing your data loss prevention (DLP) solution is a major transition that can feel overwhelming. But...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.



