Android

Advance Your Ransomware Defenses
Ransomware isn't new. In fact, it's 30-years-old . What IS new is ransomware's sudden rise as a favored...

Omnichannel Loyalty
For as heartfelt of a topic as it is, navigating the world of loyalty technology can be a real pain....

Inside The Mind of a Hacker 2019
The first step in cybersecurity? Think like a hacker. According to a recent report, 71% of cybercriminals...

Web Coding and Development All-in-One For Dummies
Speak the languages that power the web. With more high-paying web development jobs opening every day,...

Beyond the Cubicle: Life in the Digital Workspace
These days, rarely is the modern workplace a static location where employees go everyday to be productive....

A Unified Workspace delivers a transformative employee experience
A critical business edge comes from employees who are engaged, inspired and happy–thanks to the right...

Insurance MFA case study – on-premise and multiple integrations
UNIQA Czech Republic is part of one of the leading insurance groups, UNIQA, located in Austria, Central...
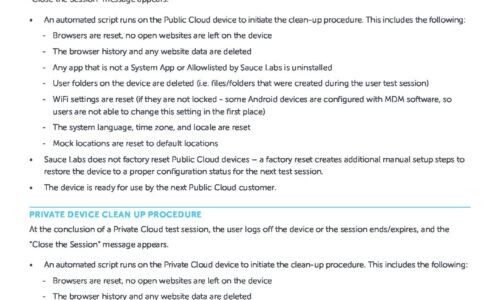
Public & Private Device Clean Up Procedure
This data sheet explains the options available when you want to make sure that your content, or some...

Common Browser Isolation challenges, and how to overcome them
A growing number of security teams are implementing a Zero Trust security strategy, in which no application,...

2022 Threat Report
The BlackBerry 2022 Threat Report is not a simple retrospective of the cyberattacks of 2021. It is a...

Forrester Wave, We're a leader!
VMware Carbon Black Named a Leader in The Forrester Wave™: Endpoint Security Software As A Service,...
Sign up for IT Tech Publish Hub
As a subscriber you will receive alerts and free access to our constantly updated library of white papers, analyst reports, case studies, web seminars and solution reports.


